Encryption MD5/SHA
Free
5.0for iPhone, iPad
Age Rating
Encryption MD5/SHA Screenshots
About Encryption MD5/SHA
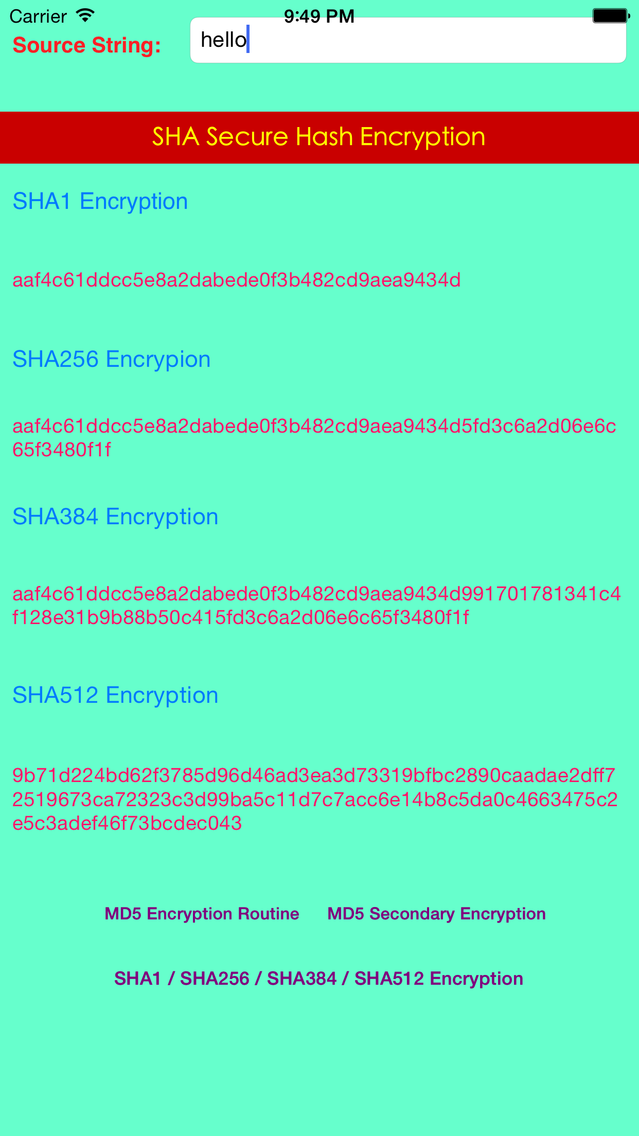
- The MD5 message-digest algorithm is a widely used cryptographic hash function producing a 128-bit (16-byte) hash value, typically expressed in text format as a 32 digit hexadecimal number. MD5 has been utilized in a wide variety of cryptographic applications, and is also commonly used to verify data integrity.
- SHA stands for "secure hash algorithm". The four SHA algorithms are structured differently and are named SHA-0, SHA-1, SHA-2, and SHA-3. SHA-0 is the original version of the 160-bit hash function published in 1993 under the name "SHA": it was not adopted by many applications. Published in 1995, SHA-1 is very similar to SHA-0, but alters the original SHA hash specification to correct alleged weaknesses. SHA-2, published in 2001, is significantly different from the SHA-1 hash function.
- SHA-1 is the most widely used of the existing SHA hash functions, and is employed in several widely used applications and protocols.
- SHA stands for "secure hash algorithm". The four SHA algorithms are structured differently and are named SHA-0, SHA-1, SHA-2, and SHA-3. SHA-0 is the original version of the 160-bit hash function published in 1993 under the name "SHA": it was not adopted by many applications. Published in 1995, SHA-1 is very similar to SHA-0, but alters the original SHA hash specification to correct alleged weaknesses. SHA-2, published in 2001, is significantly different from the SHA-1 hash function.
- SHA-1 is the most widely used of the existing SHA hash functions, and is employed in several widely used applications and protocols.
Show More
What's New in the Latest Version 5.0
Last updated on May 9, 2015
Version History
5.0
May 9, 2015
Encryption MD5/SHA FAQ
Click here to learn how to download Encryption MD5/SHA in restricted country or region.
Check the following list to see the minimum requirements of Encryption MD5/SHA.
iPhone
iPad
Encryption MD5/SHA supports English